When you think of malware, what do you envision? Many people immediately think of computer popups, viruses, or ransomware that interferes with their desktop workstations or laptops. However, cybercriminals are spending more of their time pursuing the other computing devices we all carry on a daily basis: smartphones. Mobile devices are a prime target for malware, so we shouldn’t forget that they’re vulnerable to it. Case in point, 100+ million devices in 70+ countries were recently affected by the Android malware known as Dark Herring. Zimperium, a digital security company that collaborates with Google to fight malware, called Dark Herring “the longest-running mobile SMS scam” they’ve discovered to date.
What is Dark Herring Android Malware?
Dark Herring Android malware is based on a huge network of nearly 500 innocuous-looking mobile apps that were distributed through the Google Play Store and other third-party app stores. These apps were first discovered in March of 2020, but many of them were likely circulating long before that date.
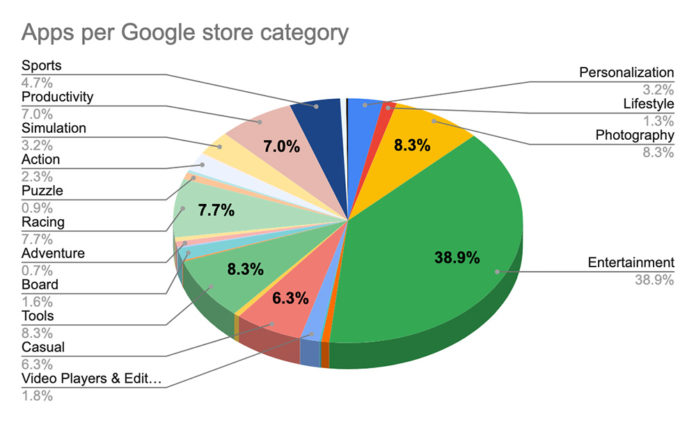
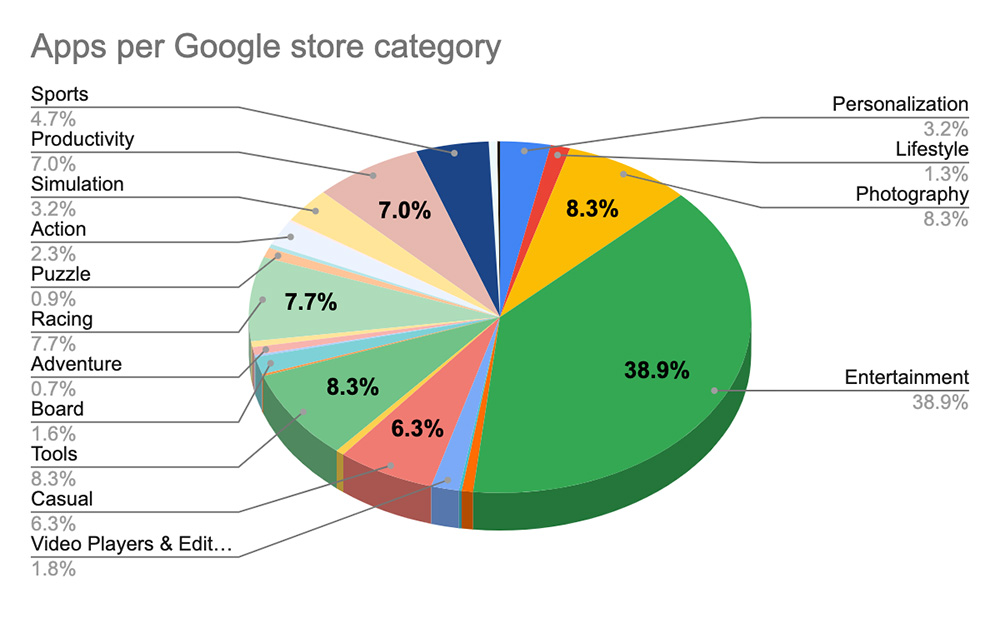
According to the Zimperium report, these apps seem relatively ordinary at first glance: “[the apps] appear harmless when looking at the store description and requested permissions.” They spanned a wide range of categories, including games, productivity tools, photo editors, phone personalization apps, and sports trackers. The apps are reportedly fully functional, so users are more likely to leave them installed long-term. “These apps are not just clones of each other or other apps, but are uniquely produced at a high rate to deceive traditional security toolsets and the potential victims.”
To make the scam convincing to a wider audience, the Dark Herring apps automatically changed their language and content based on the user’s IP address, a feature Zimperium called “exceptionally versatile.” Users in the USA would see variants of the apps meant to target English-speakers, while users in Russia or China would see versions tailored to them.
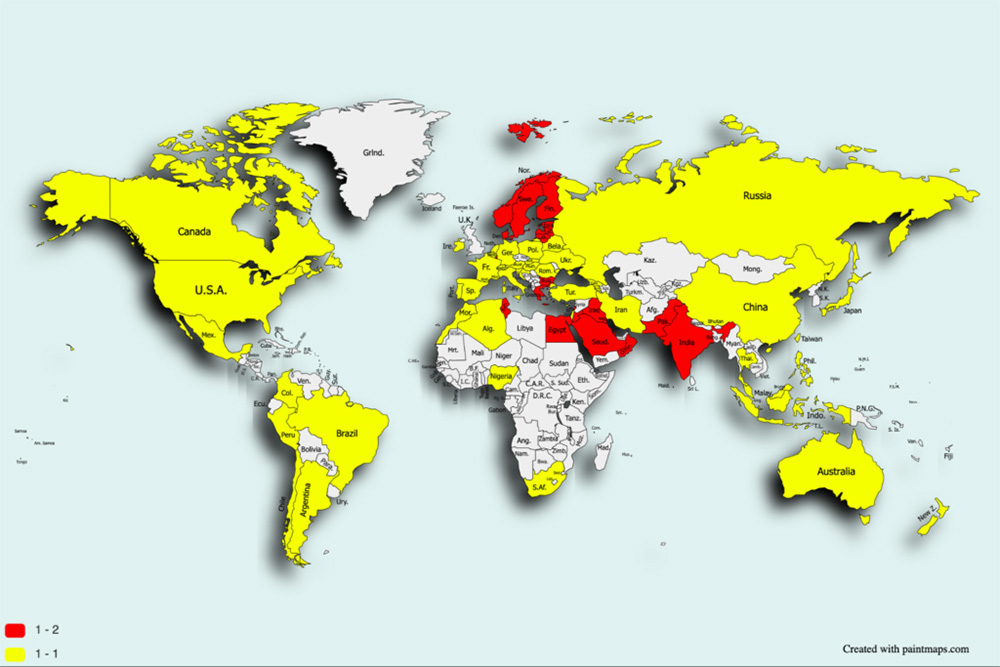
The report indicates that 70 countries were targeted by the Dark Herring Android malware applications. The map above from Zimperium indicates these countries in yellow; countries highlighted in red were assessed as higher risk due to their lack of consumer legal protections that would help victims recover money lost to mobile phone billing scams.
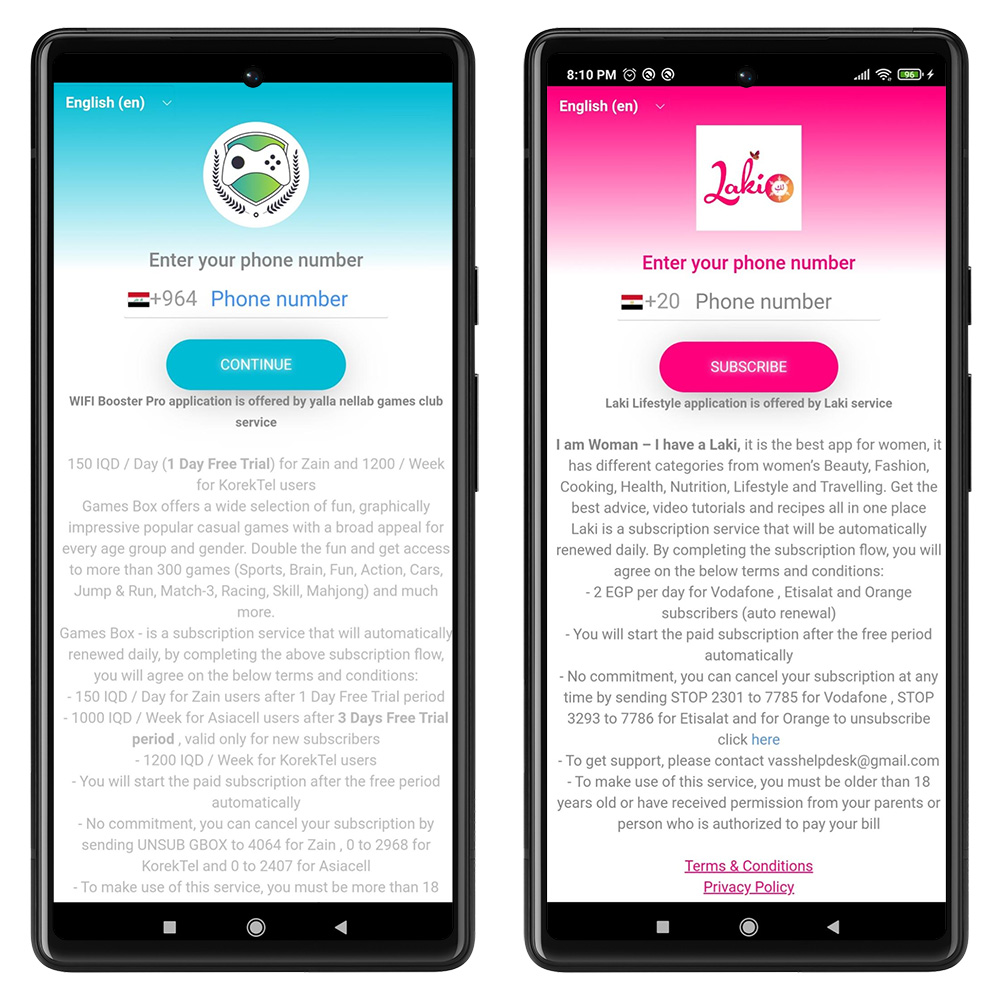
Once users installed one of the malware apps, they were eventually directed to a page that asked for their phone number. This might have seemed like an ordinary 2-factor authentication check, but it was more sinister. Zimperium writes, “In reality, they are submitting their phone number to a Direct Carrier Billing service that begins charging them an average of $15 USD per month. The victim does not immediately notice the impact of the theft, and the likelihood of the billing continuing for months before detection is high, with little to no recourse to get one’s money back.”
Download statistics show that more than 105 million Android devices around the world have installed at least one of these malicious Dark Herring apps. Zimperium’s statement reinforced the relatively sophisticated nature of this criminal enterprise: “The cybercriminal group behind this campaign has built a stable cash flow of illicit funds from these victims, generating millions in recurring revenue each month, with the total amount stolen potentially well into the hundreds of millions.” The hundreds of varied apps under the Dark Herring umbrella also provide command and control (C&C) data to the creators in a systematic manner, indicating that the malware developers built these varied apps to work together as a system. This seems to have inspired the name — these Android malware apps are like individual fish in a cohesive school.
Current Status and Lessons Learned
Thanks in part to the Zimperium report, Google has removed all the known apps related to this Android malware from the Google Play Store. The scam services and phishing sites related to these apps have also reportedly been deactivated. However, Zimperium says the Dark Herring malware is still available through third-party app stores, and is likely still present on millions of devices, creating an opening for the creators to victimize the same devices with new scams at a later date.
As a result of the huge profits generated by Dark Herring, it seems likely that the creators will apply their skills toward new forms of malware in the future.
This should serve as a reminder to be wary about the apps you install on your smartphone or tablet. Even if apps seem legitimate, have positive reviews, and are available through official app stores, these factors are not guarantees that they’re not malicious. If an app seems suspicious, consider whether you really need it, and read all the fine print carefully before submitting any personal information (including your phone number).
For more cybersecurity tips, check out our previous articles:
- Cybersecurity and Travel
- Verification Code Scams: Circumventing 2-Factor Authentication
- Human Firewall: How to Protect Yourself Against Cyber Crimes
- Infographic: The Rise in Smartphone Security Threats
Related Posts
The post Android Malware: 105 Million Users Victimized by “Dark Herring” Apps appeared first on RECOIL OFFGRID.