The digital spaces that society has become virtually dependent upon over the last 10 to 15 years are increasingly becoming nonpermissive. Big Tech censorship, intelligence organizations, and law-enforcement agencies continue to push against the First Amendment rights of Americans in ways that were previously only encountered by those living in overtly authoritarian regimes such as Iran, China, or Russia. While covert communications are often depicted as suspicious in film and politics, Steganography is a method to keep private communications secret in the digital age.
It’s not surprising then, that many people have been turning to secure communications (COMSEC) tools such as Signal or Keybase, both of which provide end-to-end encryption. COMSEC is essential, protecting the contents of your communications, whether you’re chatting with family members on Signal or accessing your online banking via HTTPS. Sometimes, COMSEC isn’t enough to protect your privacy or security, however.
Glossary
COMSEC: Communications Security
COVCOM: Covert Communications
Cover File: An image or video containing a hidden file within it
Message File: The secret message we want to hide
OPSEC: Operational Security
Dead Drop: A physical or digital location where files or items can be left by one party and retrieved by another without the two directly interacting. See Issue 37 for examples of physical dead drops.
Tradecraft: The application of tools, tactics, and procedures by intelligence or cybersecurity professionals
The Problems with Cryptography
When operating in a nonpermissive space, traditional cryptographic systems like PGP or modern systems like Signal provide two key disadvantages:
1. They do nothing to hide the fact that a communication has taken place.
2. The cryptography itself provides non-repudiation of the message by mathematically tying it to the owner of a signer’s private key.
Taken together, this means an adversary with means will know who is talking to whom and, should the keys be recovered or the messages decrypted via cryptanalysis, you won’t be able to make the case that you weren’t the one doing the communicating.
Introducing Covert Communications
Intelligence officers and their agents have had this problem for centuries, and so over that period of time many methods to hide the fact that a communication even took place. Rather than COMSEC, these techniques make up COVCOM, or Covert Communications. In the analog world, COVCOM techniques have included disappearing ink and microdots. In the digital world, one of the more common techniques is steganography.
Digital steganography is the process of encrypting a file and then embedding it into another in order to hide its existence. Typically, the encapsulate is an image or video file, as data can be encoded into pixels without affecting the appearance of the image to the human eye.
Getting Started with Steganography
There are many free software options for steganography, with options available for all major operating systems. One very popular option is called OpenStego. Written in Java, it can run on Windows, Mac, Linux, or any other OS with support for Java. This makes it an excellent choice for adoption by a MAG or other group.
OpenStego can be downloaded from https://www.openstego.com and the Java Runtime Environment (JRE) can be downloaded from https://www.java.com, if necessary.
Once you’ve got Java and have downloaded the OpenStego zip file, unzip it and look for the appropriate starter. On Windows, you’ll want the “openstego.bat” file:
Running the .bat file should start the application:
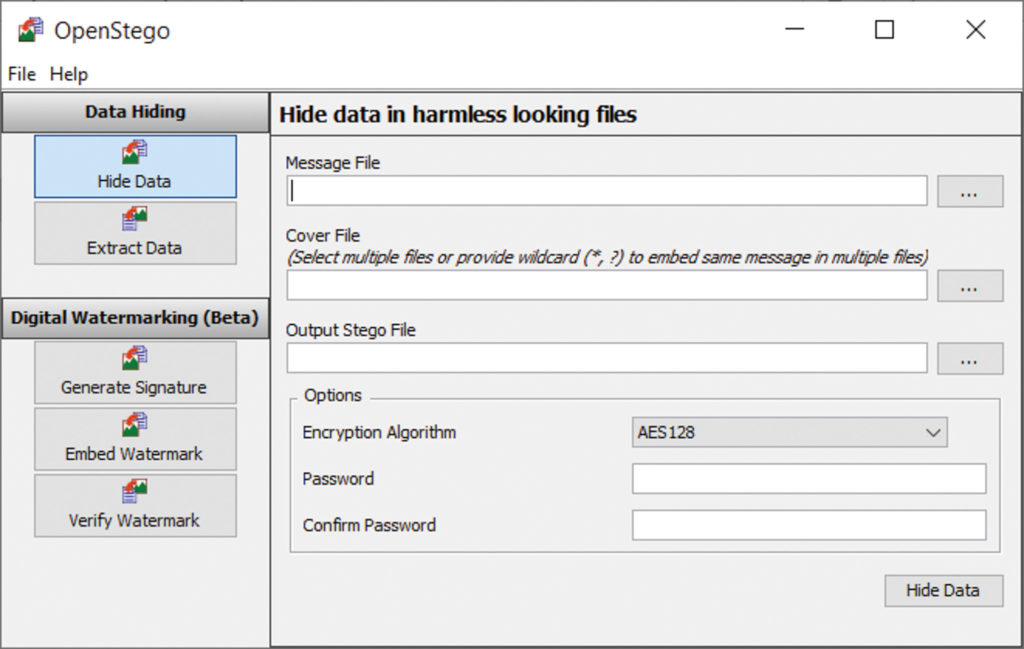
We see here that we need four things:
- Message file is the secret text or other file that we’re trying to hide.
- Cover file is the file we want to embed our message into, and what the world will see.
- Output Stego File is the name of the file that we want to create, which will be the combination of our message and the cover file.
- Encryption algorithm selection and password. This is something that’ll have to be known to all the intended recipients of the file and is used to protect the contents of the message even if its existence becomes known to an adversary.
Walking Through an Example
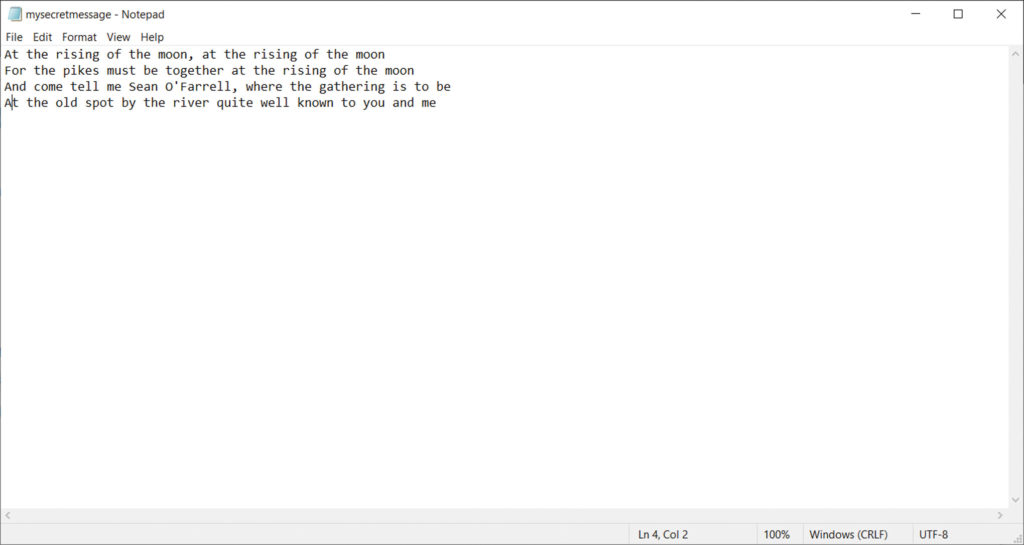
Let’s say that Big Tech has shut down a group used to organize an event or group of people, but the group still wants to organize. We may have an invitation such as this:
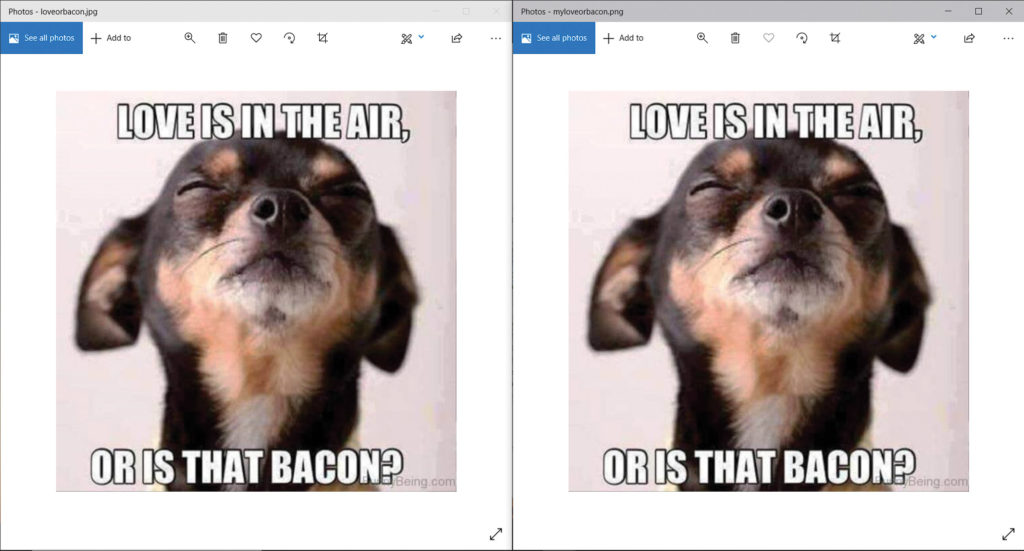
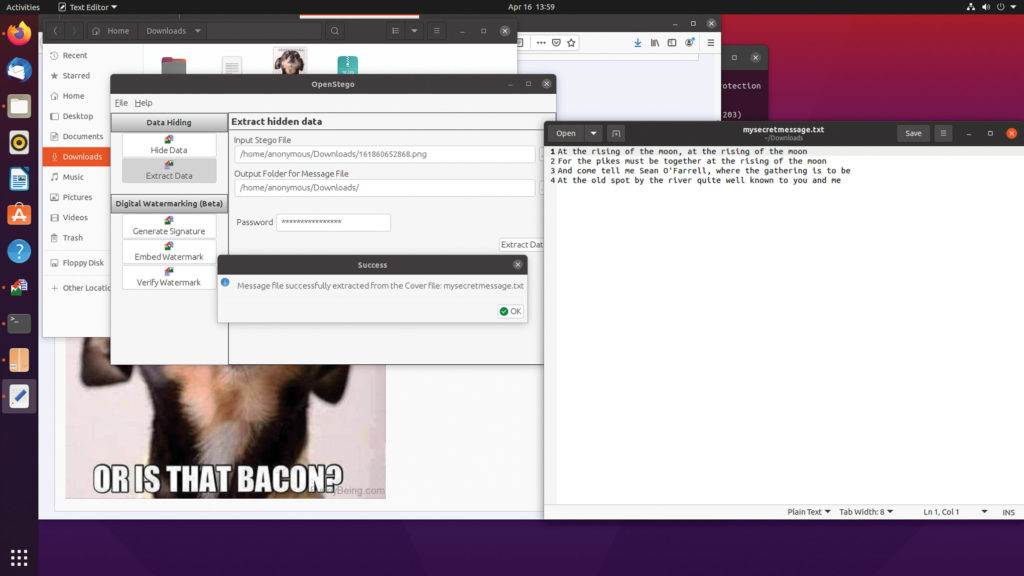
(This, of course, being a verse from the Irish rebel song “Rising of the Moon.”) We would save this file and then find some image file to hide it in. After running the program, we’d have two images. Side by side, they’d be indistinguishable:
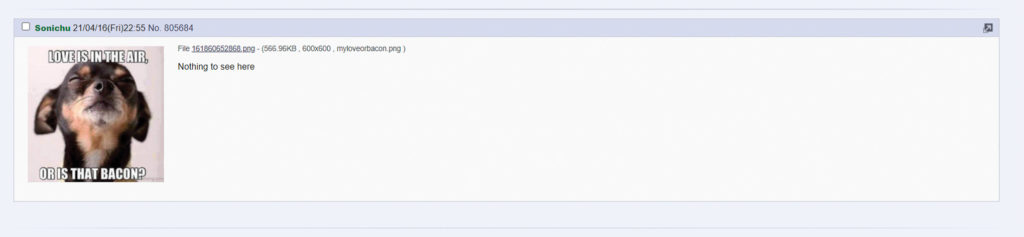
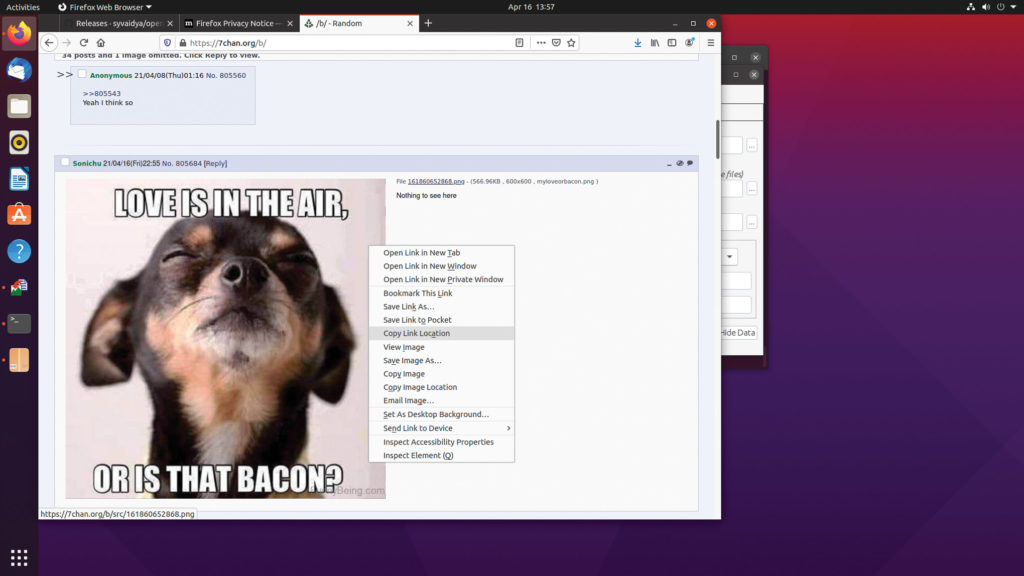
We would then post this image someplace:
Later, another group member comes by, sees the message, and downloads the image:
Using OpenStego, the member inputs the shared secret password and is able to recover the message:
Notes on Tradecraft
Tradecraft is sum of the tools, techniques, and procedures (TTPs) used by intelligence or cybersecurity professionals. Adoption and proper application of these TTPs is key to successfully operating in the increasingly nonpermissive digital space and to making use of steganography worth it.
First, the dead drop isn’t really dead. (See sidebar for a definition and refer to Issue 37 for a detailed look at real-world dead drop applications.) Websites like 4chan or 7chan, for instance, allow anonymous users to post image files, making excellent digital dead drops. The reasonably high volume of traffic, coupled with the anonymous nature of these sites, help to confuse any links between visitors. Keep in mind, however, that some of these sites have controversial profiles that may make them targets of surveillance. Throwaway profiles and free image hosting sites like Imgur.com are also good options.
Above: Steganography can be applied to any photo, but it’s often advantageous to use commonly shared memes or generic images that can be hidden in plain sight. Be sure the cover file you use fits the theme of the site you post it on.
Secondly, the digital-analog of a surveillance detection run would be leveraging Tor or a VPN before accessing any site that’ll be used as a digital dead drop. For a further layer of operational security (OPSEC), consider doing so away from your home or place of work.
Thirdly, when choosing cover files, you want to find files that are big enough that when your message is embedded, the overall size of the output file won’t be cause for obvious note. Additionally, choose cover files that are a good fit for the site you plan to dead drop them on. Common memes are always a good bet, but “adult” images on image sharing boards dedicated to the topic can be a fit, depending on your comfort level and risk profile.
Fourthly, remember to sanitize your clear text data when not using it. On Linux systems, for instance, you can securely delete files with the shred command (available as gshred on Macs). Windows systems will require a third-party software program to accomplish this. If you’re using a “live” operating system image like Tails when conducting the work, then all information is ephemeral anyway.
Last, but not least, keep in mind that there are some concerns related to the fact that everyone has to be aware of the same shared secret for this scheme to work. Failure to consider OPSEC when distributing the key to your group may provide an opportunity for a well-positioned and resourced adversary to gain information about the structure of the group. This infiltration could completely undermine your ability to set up covert communications channels. Choosing long pass phrases that are easy to remember but hard to guess will also decrease the likelihood of you or one of your peers needing to write it down, and the likelihood of an adversary being able to guess it.

Conclusion
The movement toward private and secure communications that began with Edward Snowden’s revelations of illegal domestic spying by U.S. intelligence has picked up steam since the general chaos that was 2020. While secure communications should be a cornerstone of everyone’s communications plan, the increasingly nonpermissive environment created by Big Tech and government censorship means that covert communications will become ever more important. Thanks to a proliferation of free software tools, anyone with common sense and a little basic tradecraft can integrate COVCOM into a well-rounded digital communications plan, whether for their family, their emergency preparedness group, or even just for fun.
[Illustration by Cassandra Dale.]
More on Digital Security
- What if you are the victim of Doxing? Security in the Digital Age.
- Intro into SDR: Software Defined Radio.
- 5 Ways to Protect Your Wifi Network.
Related Posts
The post Steganography: More than Meets the Eye appeared first on RECOIL OFFGRID.