Sticky notes provide a quick and easy way to write down snippets of important information — phone numbers, addresses, appointments, website URLs, and so on. But these colorful scraps of paper are low-tech tools in a high-tech world. With an NFC Tag Reader, storing vital information discreteley goes digital.
If you could design a modernized Version 2.0 of a sticky note, what characteristics would it have? It might be more durable, and water-resistant so it won’t become illegible if it gets wet. Maybe it’d be smaller, but with the capacity to store more text. Most importantly, the data it contains — letters and numbers are a form of data, after all — should be easy to access at a moment’s notice. These “advanced sticky notes” might incorporate some technology, but they shouldn’t rely on access to the internet or the power grid. And for the security-conscious user, these notes should be concealable in discreet locations and should offer optional password-protection to deter prying eyes.

They can remain readable for more than a decade.
Near Field Communication or NFC tags serve as a compact, concealable, and versatile means of storing small amounts of data. Think of them as digital sticky notes — they can be bought by the dozen for a few bucks, programmed instantly with a smartphone app, and placed almost anywhere.
What is NFC?
Near Field Communication is a radio communication standard similar to Wi-Fi, Bluetooth, or RFID, but as its name indicates, it’s intended for extremely short range. NFC devices transmit on the 13.56 MHz frequency over a maximum distance of about 4 inches. NFC’s most common use is for contactless payment systems, which allow a chip in your credit card or smartphone to wirelessly transmit payment information to a nearby point-of-sale terminal. NFC tech can be used for countless other purposes, which we’ll discuss more below.
What is an NFC Tag?
An NFC tag is a tiny wireless device that contains a small amount of memory, a radio chip, and an antenna. NFC tags don’t contain a battery; they draw the minuscule amount of power they need from the reader (e.g., your smartphone) via magnetic induction. They’re typically about the diameter of a quarter and can be fully encased in waterproof polymer or attached to a paper-thin, flexible sticker. Many colors and designs are available, and users can write on plain tags with a permanent marker. Most modern NFC tags are rewriteable, so they can be used over and over for decades. It’s also possible to lock tags in “read only” mode so they can no longer be edited. Some NFC tags support optional passwords and/or encryption to enhance security.

Buy from a reputable seller to ensure you’re getting current-generation, reliable tags.
There are myriad NFC tag variants, each with different storage capacities, transfer speeds, features, and price points. For the purposes of this article, we bought a small pack of 20 NFC tag stickers from Amazon for $15 including overnight shipping. They’re based on the NTAG216 chip and offer 888 bytes of usable memory. This chip is rated for 10 years of data retention and 100,000 read/write cycles.
How Do I Read and Write Tags?
Thanks to the prevalence of contactless payment systems like Google Pay and Apple Pay, most modern smartphones contain NFC hardware. To check if your phone is NFC-compatible, refer to the running list on Wikipedia.
If your phone supports NFC, you’ll just need to confirm that the appropriate setting is enabled and download an NFC reader app. For this article, we used an iPhone 11 and installed a free app called NFC Tools. The app makes it simple to read, write, erase, password-protect, and lock tags.
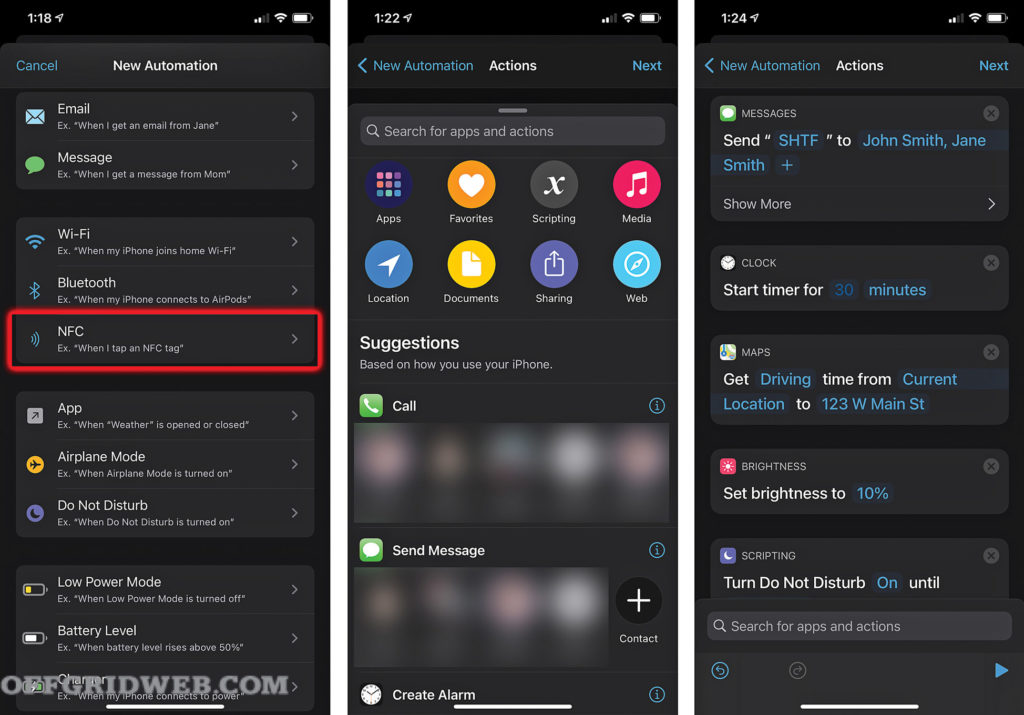
In addition to manually programming tags with text or other data, you can use automation apps to link your NFC tags to specific actions — set an alarm, send a text message, navigate to a destination, etc. On iPhones this is included in the built-in Shortcuts app; for Android phones, you can download a third-party automation app such as Tasker. See this sidebar for more details on NFC tag automation:
Automating Tasks with NFC Tags
As we mentioned earlier, NFC tags can be used in conjunction with automation apps to trigger complex sequences of actions. For example, let’s say an emergency has occurred and you need to send text messages to each member of your family, start the navigation app on your phone to check traffic conditions, dim the screen to conserve battery, and turn on do-not-disturb mode for any incoming calls outside your inner circle. These tasks could be completed by swiping your phone over a “SHTF” tag that does it all instantly.
If you’ve already integrated “smart home” features into your house, you could tie these into your NFC tag automation sequence. Remotely turn on the lights, crank up the volume on the TV, and activate your security system to convince potential intruders to pick a different house. Lock your computer or go full scorched-earth and wipe the hard drives. Activate a string of Wi-Fi-enabled Christmas lights that could hypothetically be wired into various booby traps (for legal reasons, that’s a joke). The sky’s the limit.
On a more practical note, NFC tags are great for saving time on simple daily tasks. Slap one on your washing machine to start a timer that alerts you when clothes are done. Put one in the phone cradle in your car that pairs the Bluetooth and starts a music playlist. Place one in a medication bottle that tracks each time you take a pill and activates a reminder if you forget to do so.
The catch is that the instructions for these automation sequences are stored on your phone, not on the tag. That means it won’t work with someone else’s device unless you apply the same settings in advance.
Uses for NFC Tags
Now that we’ve got the technical details out of the way, we can move on to the fun stuff.
As we mentioned above, NFC tags have only a small amount of memory. Our NTAG216 chip can store 852 characters of plain text. It’s possible to find non-standard NFC tags that can store several times that amount, but these will be much more costly and potentially unreliable with certain readers. Thankfully, there’s still a lot we can do with this limited space. Read on for a few noteworthy examples.

You can even mark tags with a Sharpie to denote their functions.
Store Emergency Information
Here’s a straightforward one that harkens back to our sticky note analogy. A tag can be programmed with emergency contact phone numbers, addresses, or coordinates for a bug-out location. In the event that you lose your wallet, you might store your driver’s license number and insurance info on a tag in your vehicle. If you need to stash some money discreetly, you could put funds on a prepaid debit card, save the info on your NFC tag, and shred the physical card. The same technique could be used for an emergency prepaid phone card. Of course, take precautions to ensure this information doesn’t fall into the wrong hands — conceal the tag, add a password, or both.
Show Proof of Ownership
If you’re looking to prove you own a piece of valuable property, you could attach a label with your name and address, but that’s easy to remove and poses some privacy concerns if it falls into the wrong hands. A hidden NFC tag containing the same information will be just as effective but much harder for thieves to notice.
Link to a File or Website
Although NFC tags don’t have much local storage capacity, they can certainly provide a link to data that’s hosted elsewhere. This can be used to save someone the trouble of typing in a website URL, or it can provide a private link to download files. Those files could be encrypted, turning the NFC tag into a digital key that unlocks a huge archive of sensitive documents cached online.
Store a Password
When you go on vacation, you might hide a key in a secure spot in case a trusted friend or neighbor needs to enter the house in an emergency. NFC tags can be used in a similar fashion to store passwords in an innocuous place. This way, you can tell the house-sitter to hold their phone up to a specific picture frame in the hall to instantly retrieve a gun safe code or security system override code.
In less dire circumstances, it’s a good way to share your Wi-Fi password with visitors without repeatedly explaining the spelling and capitalization.
Dead Drops
In Issue 37, Tom Marshall explained the Cold War spycraft technique known as a dead drop. This involves two parties covertly exchanging information without making direct contact. For example, one agent would leave a note in a hidden location and give a predetermined sign that a drop was ready — a chalk mark on a mailbox or a piece of tape in the corner of a window. A second agent would see the sign and retrieve the drop.
Large amounts of digital information might require a USB drive loaded with files, but this can be risky, since anyone who sees it will know it contains data. On the other hand, most people would never guess that an NFC tag contains data, much less consider how to retrieve it. It’d be easy to write a few sentences onto a tag and stick it inside a book jacket, onto the underside of a bench, behind a car’s fuel door, or in thousands of other creative locations. The recipient would only need to scan the tag from a few inches away and could rewrite a response without leaving so much as a fingerprint.
For added security, apply a password, encrypt the tag, or encode the message itself with a cipher.

Nearly Infinite Possibilities
Much like the ubiquitous sticky note, NFC tags are nothing more than repositories for small amounts of information. You can write anything you wish onto them, from a simple phone number to an encryption key that unlocks every one of your digital assets. Despite their relatively small capacity and short range, they’re incredibly versatile, especially when they’re paired with automation apps that can control your smartphone or home appliances. Pick up a few and start experimenting — you’ll be surprised by all you can accomplish with a single swipe.
More on CyberSecurity and Discreet Communication
- CyberSecurity and Travel
- What if you are the victim of Doxing? Security in the Digital Age.
- Intro into SDR: Software Defined Radio.
- 5 Ways to Protect Your Wifi Network.
- Steganography: Hiding Messages Inside Boring Images
Related Posts
The post NFC Tag: A Close Look at Near Field Communication Technology appeared first on RECOIL OFFGRID.